How Do I Recall A Text
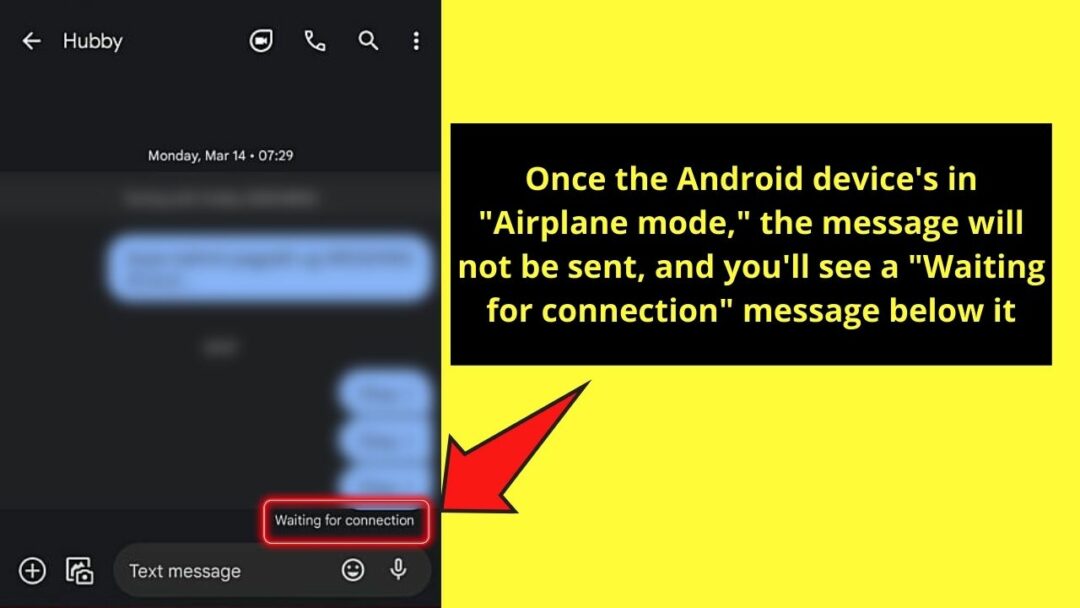
Okay, let's talk about recalling a text message – something you can't actually do in the physical world, but we're going to use the analogy of a car recall to understand how data, once sent, can be a tricky beast to handle. Think of your phone as the engine control unit (ECU), the text message as a command sent to other parts of the car (another phone), and the "recall" as trying to undo that command. While you can't literally yank a message back from someone's phone (unless they're within Bluetooth range and you have some seriously advanced hacking skills, which we definitely don't condone or advise), understanding how data networks function can help you appreciate the challenges and limitations.
Purpose: Understanding Data Persistence
Why are we drawing parallels between cars and text messages? Because it helps illustrate the concept of data persistence and the challenges of real-time communication. Just like a faulty command sent to a car's transmission can't be undone once the transmission has shifted gears, a text message, once delivered, exists independently on the recipient's device. This understanding is crucial for:
- Appreciating Data Privacy: Knowing that sent data is difficult (if not impossible) to truly erase emphasizes the importance of being mindful of what you share.
- Troubleshooting Network Issues: Understanding the flow of data helps diagnose communication problems, even if you can't literally "recall" anything.
- Building Secure Systems: This knowledge is essential for developers creating applications where data integrity and security are paramount.
Key "Specs" and Main "Parts"
Instead of car specs, let's consider the components of a basic text messaging system. Think of it as a simplified data flow diagram:
- Sender's Device (Your Phone): The initiation point. It acts like the driver and control panel, inputting the message and initiating the send command.
- Text Messaging Application (e.g., Messages, WhatsApp): This is your interface. It encodes the message, handles the formatting, and communicates with the network. Think of it as the gas pedal and steering wheel.
- Mobile Network Operator (Carrier): This is the road network and traffic control. They handle the transmission of the message from your device to the recipient's. It's responsible for routing the data.
- Short Message Service Center (SMSC): A component within the carrier's infrastructure that acts as a temporary storage facility for messages, especially when the recipient's device is unavailable. This is like a parking lot.
- Recipient's Device (Their Phone): The destination. It receives, decodes, and displays the message.
A key "spec" to understand is that SMS (Short Message Service) and MMS (Multimedia Messaging Service) are *store-and-forward* technologies. This means the message isn't sent directly to the recipient in real-time. It's stored at the SMSC and forwarded when the recipient is available. This creates a delay and makes true recall impossible.
"Symbols" – Data Flow Representation
Instead of electrical symbols, let's use common flowchart symbols to represent data flow:
- Rectangle: Represents a process (e.g., Encoding Message, Sending Message).
- Diamond: Represents a decision (e.g., Is Recipient Available?).
- Arrow: Represents the flow of data (e.g., Message Data).
- Cylinder: Represents data storage (e.g., SMSC).
Imagine a simple flowchart:
[Start] -> [Enter Message] -> [Encoding Message (Rectangle)] -> [Send Message (Rectangle)] -> [Carrier Network] -> [Is Recipient Available? (Diamond)]
| Yes -> [Deliver Message to Recipient (Rectangle)] -> [End]
| No -> [Store Message in SMSC (Cylinder)] -> [Check Recipient Availability Later] -> ... (Loop)
The crucial point is that once the "Send Message" process (rectangle) is complete and the data hits the "Carrier Network," you've lost direct control. The data is now being managed by the carrier's infrastructure.
How It Works – The Data Pipeline
Let’s break down the journey of a text message:
- Composition: You type your message in your messaging app. The app encodes it into a format suitable for transmission. This encoding might involve compressing the data and adding headers for routing information.
- Transmission: The encoded message is sent from your phone to the nearest cell tower, then relayed through the mobile network to the SMSC.
- Storage (Potential): If the recipient's phone is off or out of range, the SMSC stores the message. It will periodically attempt to deliver the message until it succeeds or the message expires (usually after a few hours or days).
- Delivery: Once the recipient's phone is available, the SMSC forwards the message to their device. Their phone decodes the message and displays it.
The *crucial* step where recall becomes impossible is when the message leaves your device and enters the carrier's network. You no longer have direct control over the data.
Real-World Use – Troubleshooting "Undelivered" Messages
While you can't "recall" a sent message, understanding this data flow helps with troubleshooting:
- Message Stuck "Sending": This likely indicates a problem with your device or your connection to the mobile network. Check your signal strength, restart your phone, or contact your carrier.
- Recipient Not Receiving Messages: Could be an issue with their device, their network, or your number being blocked. Ask them to check their signal strength, restart their phone, or ensure they haven't blocked you.
- Delayed Messages: This often indicates a temporary congestion in the mobile network or a delay in the SMSC. Usually, the message will eventually arrive.
Think of it like diagnosing a car that won't start. You trace the electrical system to find the fault. Here, you trace the data flow to pinpoint the bottleneck.
Safety – Data Security and Privacy
While there aren't physical hazards like high voltage, data security is paramount. Consider these points:
- Phishing and Malware: Be cautious about clicking links in text messages, especially from unknown senders. They could lead to phishing sites or malware downloads. This is like getting bad gas in your car – it can damage the engine (your phone).
- Data Breaches: Understand that mobile networks and SMSCs are potential targets for data breaches. While rare, it's a risk to be aware of.
- Privacy Settings: Review your messaging app's privacy settings to control who can contact you and how your data is used.
Just like you wouldn't leave your car unlocked in a bad neighborhood, be vigilant about your data security.
In summary, while the idea of recalling a text is appealing, the fundamental nature of store-and-forward technology and distributed networks makes it practically impossible. Understanding the data flow, however, empowers you to troubleshoot issues and appreciate the importance of data privacy and security.
Remember, this is a simplified analogy. The actual data flow in a modern messaging system (e.g., using encrypted messaging apps) is far more complex, involving end-to-end encryption and distributed servers. These complexities offer some, albeit imperfect, control over data, especially within specific app ecosystems.
We have a more detailed data flow diagram of a typical SMS system. Feel free to request it, and we'll provide a link for download.
